This blog post shows how you can identify NSGs without NSG Flow Logs and Traffic Analytics configured with Azure Monitor Network Insights.
Visualizing network traffic for your Azure networks can be a complex and long-lasting task, but luckily this is where Azure Network Watcher comes in. Network Watcher is a regional service that foresees tools to monitor, diagnose, and gain insight into the network performance between various points and resources in your Azure virtual networks (VNets).
Microsoft designed it to monitor the network health and to diagnose conditions at the network level for virtual machines (VMs), VNets, Azure Application Gateways, Load Balancers, etc., in your Azure environment.
One of the features available in Network Watcher is Network security group (NSG) Flow Logs. NSG Flow Logs enable you to capture information about IP traffic flowing in and out of NSGs and store this in information as a .json file (PT1H.json) file into an Azure Storage account. These raw logs will contain 5-tuple flow information about all traffic going through your NSGs (i.e., source IP, source port, destination IP, destination port and protocol).
Afterwards you can then use those logs to check for anomalies or to get more insight into suspected breaches. In addition, you can also download, export and use them for security compliance, security governance or for auditing purposes.
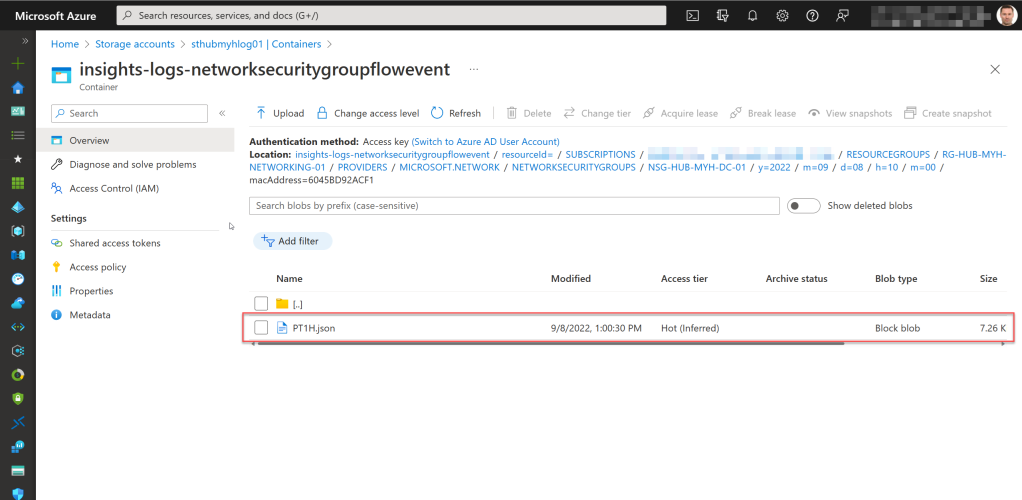
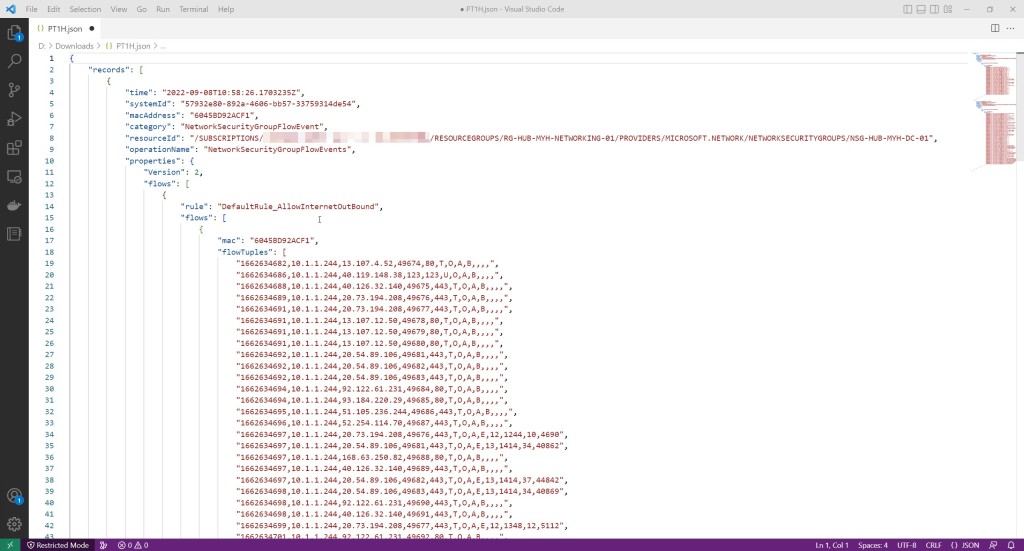
Reading the content of this generated .json file is not easy, but this is where another Network Watcher feature can be used for, namely Traffic Analytics.
Traffic Analytics is a solution that analyzes and query’s your Azure Network watcher NSG Flow Logs data and makes it more human-readable. In this way it can provide insights into the traffic flow patterns across your Azure subscriptions, but also foresee visibility into user and application activity which can help you to identify possible security threats.
For storing the resulting enhanced logs, it requires a Log Analytics workspace (NSGs can be in a different region). Keep in mind that Traffic Analytics has a metered pricing, which is based on the amount of flow log data processed by the service.
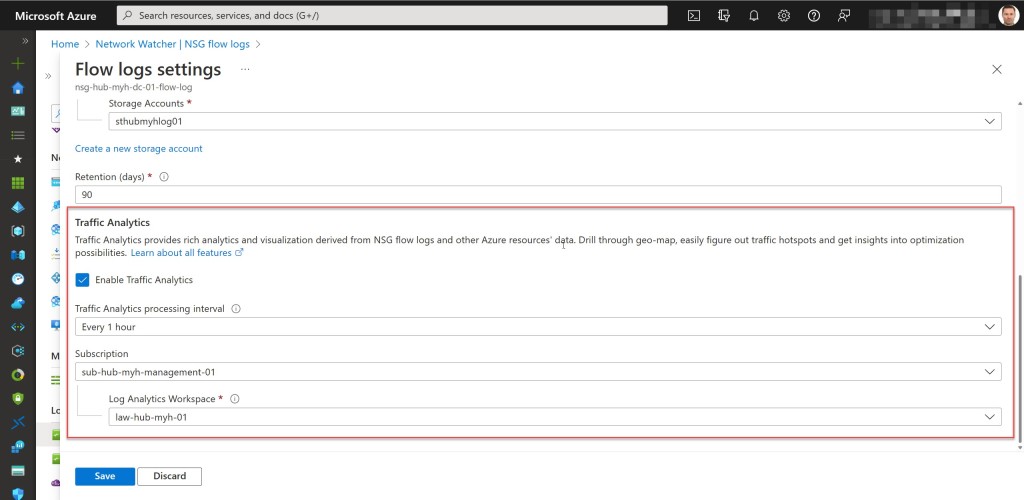
You can enable NSG flow logging and Traffic Analytics trough the Azure Portal, Azure PowerShell, Azure CLI or by using the REST API.
If you want, you can always take a look at my previous blog post which can help you to configure NSG Flow Logs with an Azure PowerShell script: Azure Networking: Configure NSG Flow Logs for all NSGs in an Azure Subscription with an Azure PowerShell script
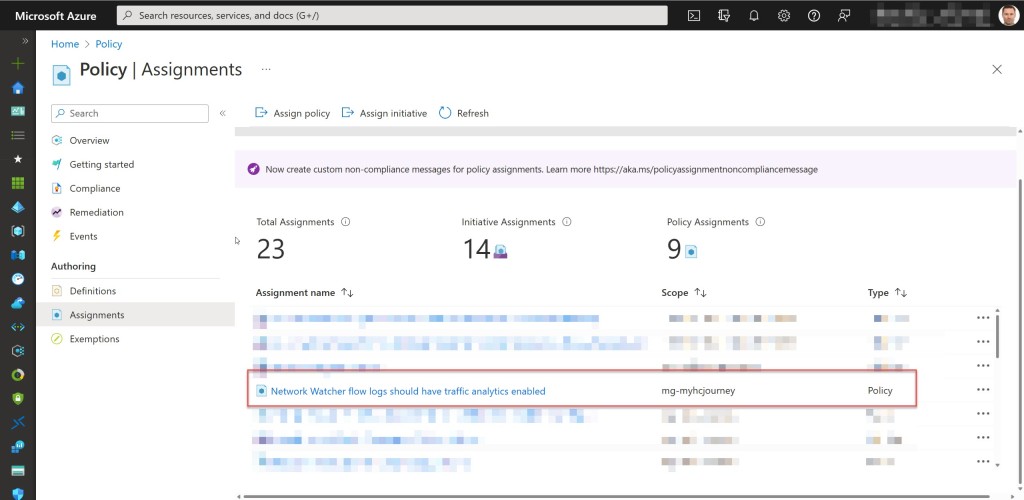
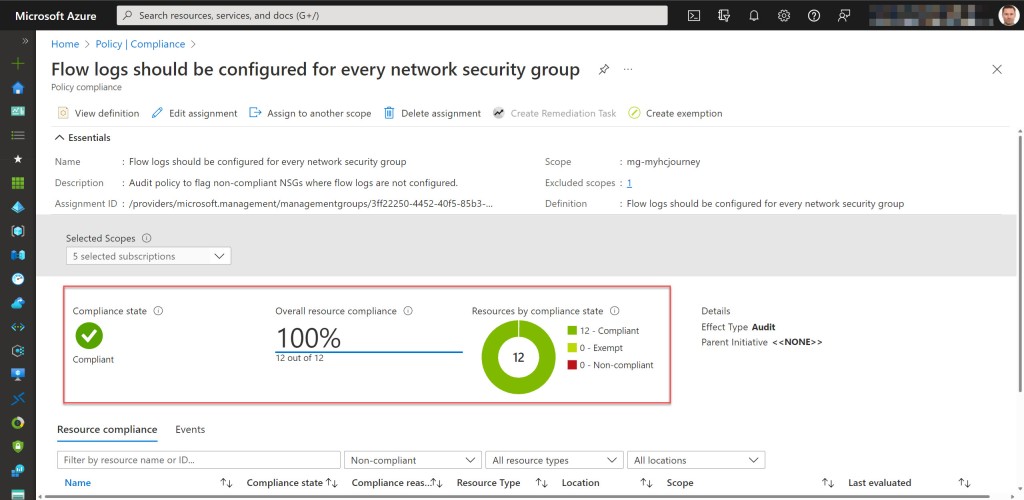
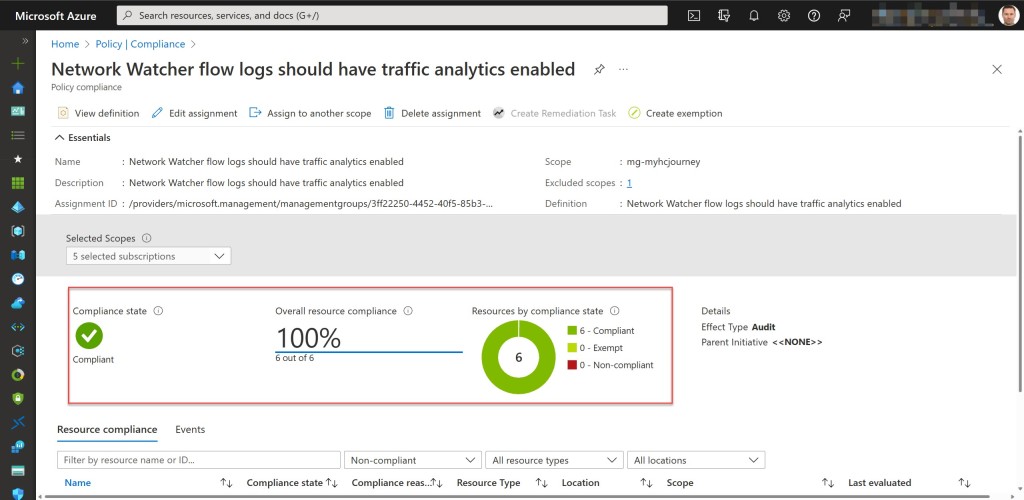
You can also use the built-in policy “Flow log should be configured for every network security group” to audit all NSGs in a given scope, and to check for the existence of linked Flow Logs. Next to that one, you can also use another built-in policy “Network Watcher flow logs should have traffic analytics enabled” to audit all NSG flow logs and to validate that if they have Traffic Analytics enabled or not.
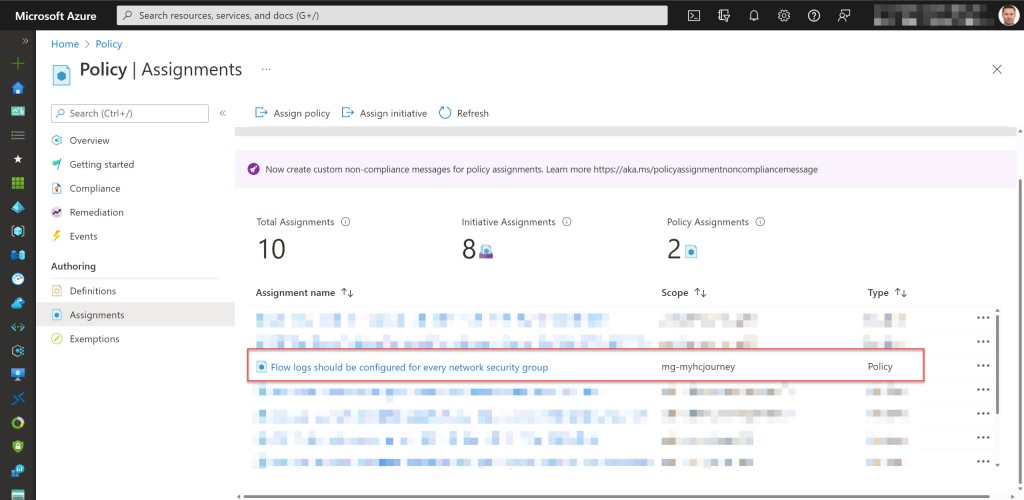
But there is also another and faster way to identify all NSGs without NSG Flowlogs and Traffic Analytics configured with the use of Azure Monitor Network Insights, which I will show in this blogpost.
Prerequisites
- A Network Watcher enabled Azure subscription(s).
- An Azure Administrator account with the necessary RBAC roles.
- An existing Azure Storage account(s), to store raw flow logs.
- An existing Log Analytics workspace.
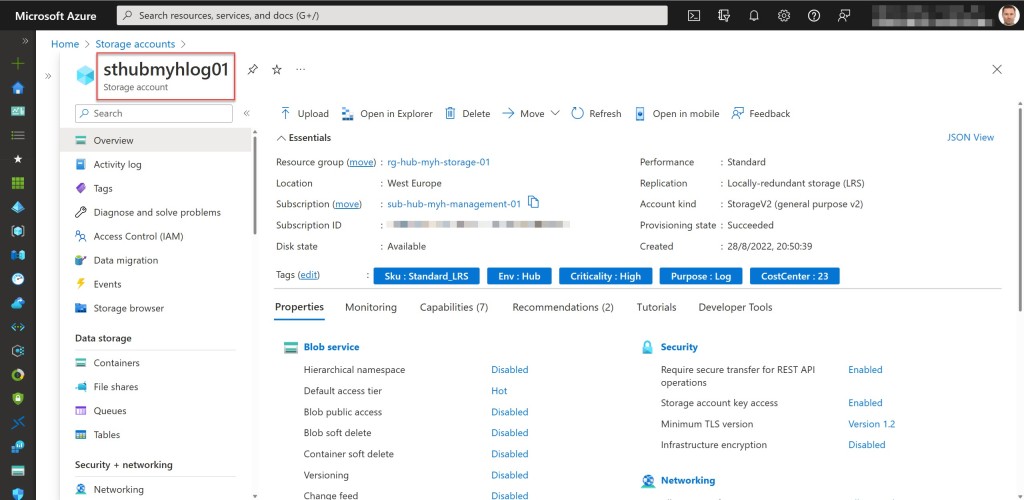
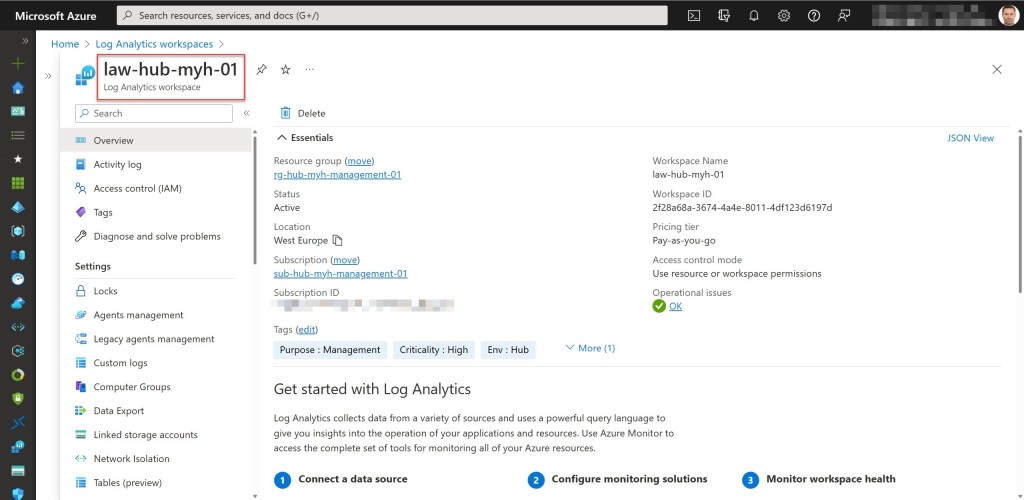
Identify NSGs without NSG Flow Logs and Traffic Analytics configured
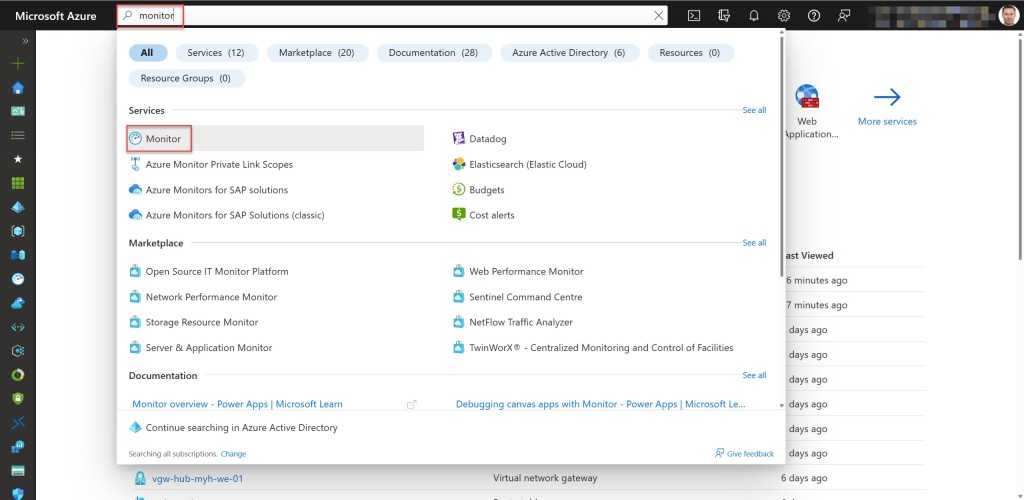
Logon to the Azure Portal and type in “monitor” in the Global search bar. Then click on Monitor.
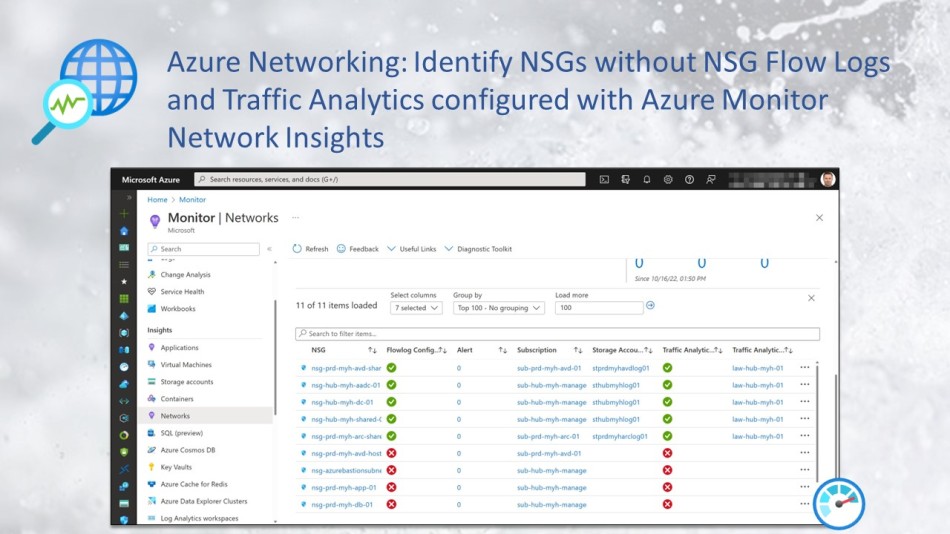
In the Monitor screen (blade), select Networks under the Insights section to open Azure Monitor Network Insights. Then click on the Traffic tab.
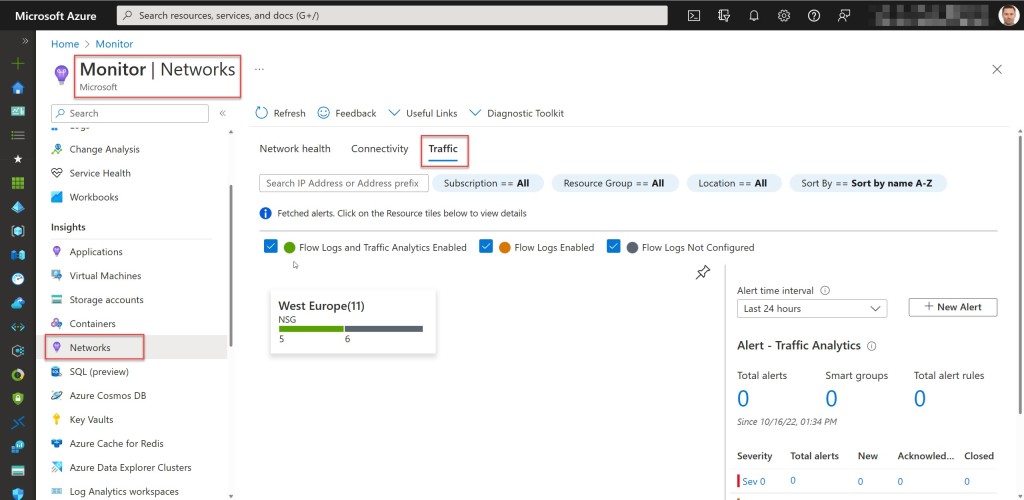
Select All your Subscription(s), All Resource Group(s) and All Location(s). Then click on a specific region tile to open a grid view which shows all NSG flow logs and Traffic Analytics settings for the NSGs in that specific region.
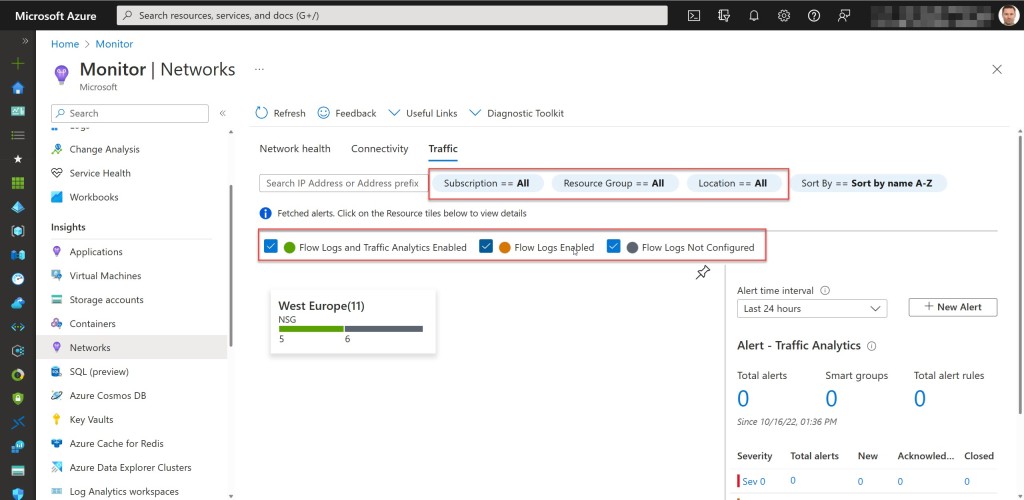
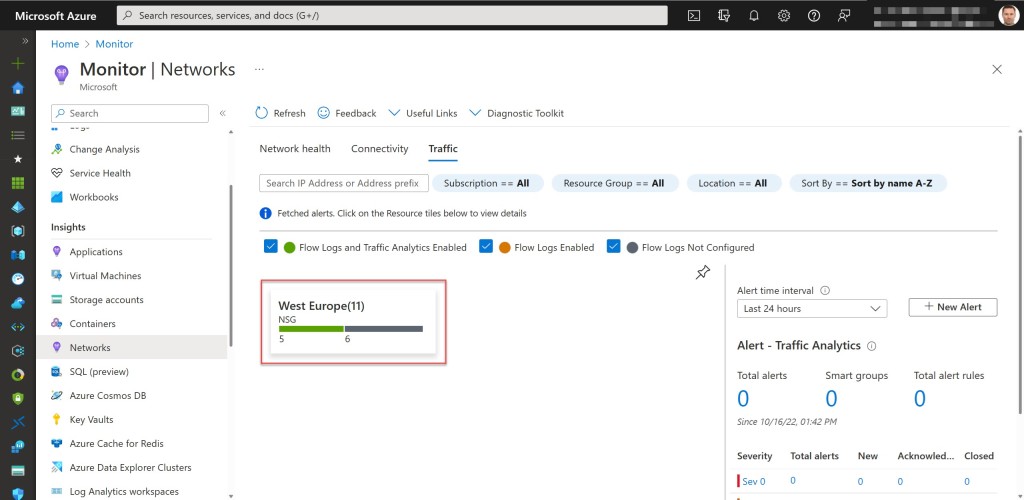
In this grid view, you can now easily find all NSGs without NSG Flow logs and Traffic Analytics configured.
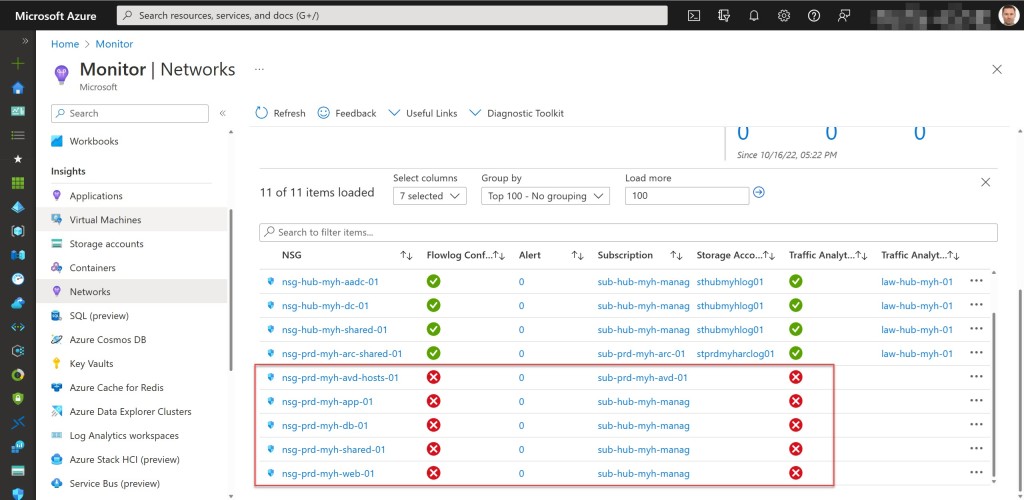
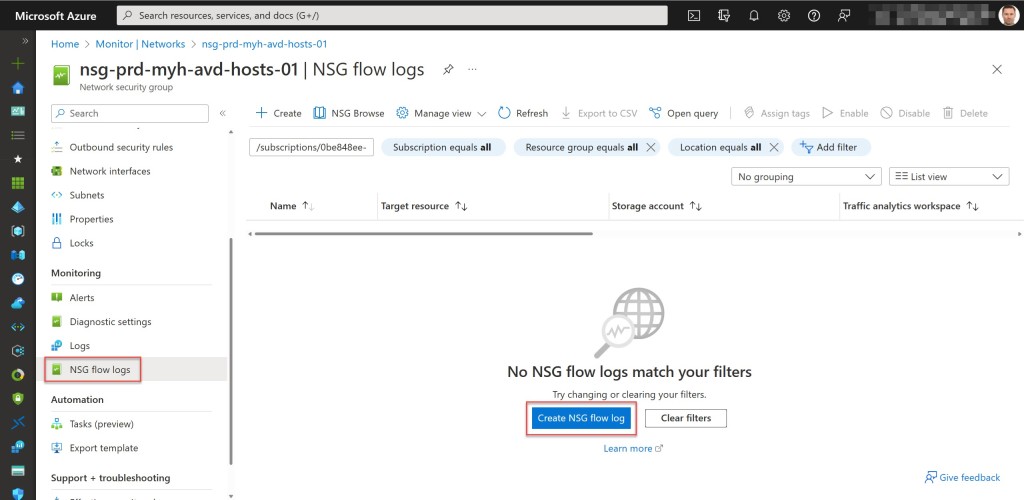
If you click on a specific NSG you can enable the NSG flow logs trough the Azure Portal, but off course it is better to automate the enabling process with the use of Azure PowerShell or Azure CLI.
Conclusion
NSG Flow Logs and Traffic Analytics are both features from Azure Network Watcher, which combined enable you to capture and visualize information about IP traffic flowing in and out of the NSGs in your Azure environment.
To identify all NSGs without NSG Flow Logs and Traffic Analytics configured with Azure Monitor Network Insights you can follow the steps shown in this blogpost.
If you have any questions or recommendations about this blogpost, feel free to contact me through my Twitter handle (@wmatthyssen) or to just leave a comment.
0 comments on “Azure Networking: Identify NSGs without NSG Flow Logs and Traffic Analytics configured with Azure Monitor Network Insights”